You’ve Got Spam
Receiving an Extortion E-mail

By: David Deschesne
Editor/Publisher, Fort Fairfield Journal
October 24, 2018
It can be pretty disconcerting to see an E-mail come in to your mailbox that looks like it originated from you. Scammers have been spoofing E-mail addresses for perhaps as long as there’s been E-mail. In the older, pre-internet days it would be the same as printing an envelope and letterhead with your name and address and mailing it to you, or one of your associates.
This scamming technique is usually done to bypass spam filters by using contact addresses that you already know and don’t filter out. From time to time I’ll get an E-mail from a scammer using my biological mother’s E-mail address as the originator and it will essentially contain “click bait” to get me to click onto a link. Since I know her well enough, I know she doesn’t forward stuff like that so when I see it I just delete it and never open any attachments or click on any links. Paypal has also suffered from similar E-mail spoofing with bad actors hi-jacking their E-mail address and using it to trick people into opening attachments and click on links.
The other day I got a slightly more aggressive scam E-mail. The text of it is:
Hello editor@
My nickname in darknet is allie94.
I'll begin by saying that I hacked this mailbox (please look on 'from' in your header) more than six months ago,
through it I infected your operating system with a virus (trojan) created by me and have been monitoring you for a long time.
Even if you changed the password after that - it does not matter, my virus intercepted all the caching data on your computer
and automatically saved access for me.
I have access to all your accounts, social networks, email, browsing history.
Accordingly, I have the data of all your contacts, files from your computer, photos and videos.
I was most struck by the intimate content sites that you occasionally visit.
You have a very wild imagination, I tell you!
During your pastime and entertainment there, I took screenshot through the camera of your device, synchronizing with what you are watching.
Oh my god! You are so funny and excited!
I think that you do not want all your contacts to get these files, right?
If you are of the same opinion, then I think that $500 is quite a fair price to destroy the dirt I created.
Send the above amount on my bitcoin wallet: 1MN7A7QqQaAVoxV4zdjdrnEHXmjhzcQ4Bq
As soon as the above amount is received, I guarantee that the data will be deleted, I do not need it.
Otherwise, these files and history of visiting sites will get all your contacts from your device.
Also, I'll send to everyone your contact access to your email and access logs, I have carefully saved it!
Since reading this letter you have 48 hours!
After your reading this message, I'll receive an automatic notification that you have seen the letter.
I hope I taught you a good lesson.
Do not be so nonchalant, please visit only to proven resources, and don't enter your passwords anywhere!
Good luck!
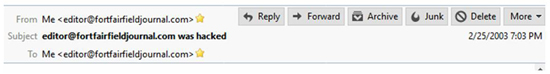
Let’s analyze this E-mail scam. First, notice the header of the E-mail which is reprinted above. At first glance, you will notice it appears to be coming from me and sent to me. As I said, this is an old trick and there is even free software out there on the net that people can download, fill in the “from” and “to” E-mail addresses and on the face of it, make it appear an E-mail originated from the address listed in the “From” line—no hack required.
However, scammers need to be careful. All E-mails are sent with a detailed computer code that in fact tells which server actually sent the E-mail. When I looked up that data for this E-mail, I found this:
From: <editor@fortfairfieldjournal.com>
To: <editor@fortfairfieldjournal.com>
Subject: editor@fortfairfieldjournal.com was hacked
Date: 25 Feb 2003 18:03:03 -0600
MIME-Version: 1.0
Content-Type: text/plain;
charset="cp-850"
Content-Transfer-Encoding: 8bit
X-Priority: 3
X-MSMail-Priority: Normal
X-Mailer: Microsoft Windows Live Mail 15.4.3508.1109
X-MimeOLE: Produced By Microsoft MimeOLE V15.4.3508.1109
You will notice at the end, the X-Mailer, which is a program that allows one to send an E-mail without an E-mail account, was Windows Live Mail and the numerical code which follows is the server identifier. Since I do not use Windows Live Mail as my server, this is the first clue that my site wasn’t “hacked” as the perpetrator insinuated. What it does show is that’s the server the perpetrator used to send the malevolent spam E-mail.
The second thing to notice is the date. It shows “2/25/2003 7:03PM”.
This is the second clue to show this if fake, and the perpetrator did not do his homework, since I didn’t start the Fort Fairfield Journal until May, 2004 and didn’t even have the @fortfairfieldjournal.com E-mail address until probably around 2010.
The perpetrator said I had 48 hours to pay the extortion fee, but he kept sending the fake E-mail for several days. He must have caught the error in the dating (which was probably a default date the E-mail spam software inserted since he neglected to fill in that field) and brought the date to current in subsequent E-mails.
The third thing to look at is in the opening salutation. He writes, “Hello editor@.” Apparently, he’s too lazy to actually research the name of the person he’s attempting to extort money from.
The next thing I cued in on to let me know it was a fake is how he indicated he knows all about my website visits and how I might be embarrassed if they were revealed to all of those on my address list. This threat has a couple of problems with it. First, I only visit news & information websites, the Maine Revised Statues and a few electronics suppliers. So, move along folks, nothing to see here. Secondly, presuming this is a legitimate hack, if he did E-mail all that information to people on my list, they would know that E-mailing such information from my E-mail account is out of character for me and would instantly consider it a hack by a nefarious actor who can’t be trusted, anyway, so they wouldn’t trust any data that was received as being real. After all, this guy’s motive is extortion, which makes him a criminal, and by extension a dishonest, disreputable and untrustworthy person who could have just as easily fabricated the files.
After wading through that bogus threat, I read how he has all the photos and videos on my computer. Okay, maybe so, but it’s just photos I take for the Fort Fairfield Journal and a bunch of videos on U.S. history and quantum physics. (He wants to be careful, my photos are copyrighted and I could track him down and sue him if he uses them without my permission!) Again, nothing to see here. As an aside, I know he can’t possibly email all that data—even if he had it—because it would be several Gigabytes and most E-mail servers limit traffic to a mere 20 Megabytes.
He then said how he has pictures of me taken from my on-screen video camera. That’s funny. My laptop video camera has a piece of black duct tape over it, and has since the day the computer came out of the box. (That’s what I suggest everyone do with those little cameras. They look like a little round piece of clear plastic at the top of the frame around your laptop screen, usually in the center. Tape them up!) So, if he indeed legitimately hacked my computer, he’d know that the video camera has been rendered unusable.
He then goes on to demand that I send him $500 to his untraceable and encrypted Bitcoin wallet, promising that once he receives the money, he will “guarantee that the data will be deleted.”
Wait a minute. If, in fact, he is legitimate and has in fact stolen my computer files, then he’s a criminal. How can anyone trust a criminal to keep his guarantee? I guess he didn’t think that through. I’ve watched enough Hawaii Five-O (the 1960’s version, which is better than the newer knock-off) to understand that whenever an extortionist demands money, either for a ransom or for material like this, there is no way to guarantee that they will honor their end of the agreement once they’re paid off. After all, they are a criminal. They could simply come back a week, or even a day later, and demand more money again. So, I learned from watching Steve McGarrett to not give in to the criminals or send them any money (This scammer also didn’t do enough research to know that I don’t even have $500 in disposable income to pay extortion fees to begin with).
I did not pay any money and I’m no longer receiving these scam E-mails—for now. I also have no reports from any of my contacts that any compromising files of mine have made their way to their E-mail servers with my address.
With that said, however, I’m sure I was just a single part of a much larger scam where hundreds, or perhaps thousands of these E-mails were bulk-mailed out to unsuspecting individuals. This scammer may have landed a few thousand dollars in con-money without actually having any of the information he purported to have. He just relied on the guilty consciences of unsophisticated victims as a means to separate them from their money.
If you get a similar E-mail, just relax a little. It doesn’t require a “hack” of your computer to Spoof an E-mail address and if any illegal activity is purported to be coming from you, the State Police Crime Lab will likely be more than able to use your E-mail’s data log to trace back to the original ISP to show that it didn’t really originate from your computer, or even your geographical area, to begin with.
With all that said, I don’t want to give you a false sense of security. Keep in mind everything you look up, read or write on a computer connected to the internet is an open book to real hackers and government. All of your Facebook posts, all of the websites you visit, etc. are all data-logged by data-mining bots for the government and they will use that information to profile you and ultimately put you in jail, if they can.
Use your computer as a tool to access information and communicate with others, but use it carefully and responsibly.








